CardLab releases its biometric FIDO authentication solution, while preparing release of a biometrically secured platform for the EU Digital wallet, using offline biometric identity verification.
For a long time, digitalisation has been all about driving efficiency and productivity, but with all sorts of Cyberattacks and ransomware showing no signs of slowing down, ignoring the cybersecurity aspect is simply no longer an option. No matter the scale of the operation, whether a global player or a start‑up, the risks and consequences are the same. Digital protection is central to safeguarding the industrial/infrastructure operations of the future, ensuring the benefits of digitalisation can be harvested, and identities and data can be kept secure.
Cybersecurity is no longer separate from performance; it is what makes high performance attainable and sustainable. Without robust protection, every productivity gain rests on shaky ground.

Biometric FIDO for secure identity verification
After FIDO (Fast Identity Online) certification and extensive field testing, this solution is now being released by CardLab as a combined physical and logical access card making use of standard NFC access control systems and FIDO logon using Bluetooth, BLE. At the same time, CardLab releases the QuardLock FIDO-certified authentication server solution, and it does so with the biometric fingerprint card from a consolidated cybersecurity platform that can keep data protection and productivity on solid ground.
The biometric SmartCard with fingerprint sensor is always offline, and the fingerprint templates are encrypted in the card and never leave it. Private keys used for authentication and transaction signing are also encrypted in the card and never leave it. By definition, nothing in the card is accessible from outside, providing a new level of hacker-proof identity verification and cybersecurity solution.
This is the solution that moves identity verification from being a device-based authentication to being a person-centric verification. With the algorithms that the fingerprint sensor runs on, it is virtually impossible to copy a fingerprint and activate the card as an authentication tool. This is also a very convenient solution as you only need to remember bringing your finger for verification and thereby eliminate the risk of having your device stolen, hacked, or your passwords compromised.
Why biometric FIDO authentication matters
History has shown that passwords are the weakest link in cybersecurity and the most common reason for data breaches. The solution until now has been longer and more complicated passwords that users cannot remember or load into a password manager that can be hacked, like what happened last year when 16 billion passwords were intercepted in one hack. That’s why it’s time to go passwordless with biometric verification of the user. Cardlab’s solution eliminates the need for passwords, providing a seamless and secure way to protect your data and your employees’ digital identity.
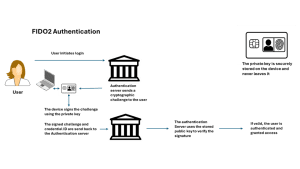
The new and more secure methods used today for authentication (FIDO2/passkey) replace static passwords and time-based codes with extremely strong public key cryptography, making it highly resistant to phishing, man-in-the-middle, session hijacking, and other types of attacks.
FIDO2/passkey requires physical access to the smartphone or device/card that holds the private key. This means that even if a hacker intercepts the communication remotely, he cannot use it to authenticate without having the physical device in his hands. Biometric verification (FaceID, fingerprint, etc.) on the device adds an extra layer of security. The highest level of user security and protection is achieved by offline identity verification, like on a biometric card, where there is no external hacker access to the device and the underlying SW, like on Smartphones.
These features make FIDO2/passkey a highly secure authentication method, significantly reducing the risk of remote attacks, which is the main method used by hackers. Using a CardLab biometric SmartCard with a built-in FIDO2/passkey feature will provide the highest level of authentication security since transaction signing happens offline, completely out of hacker reach.
Never trust, always verify
To establish and verify identities is an important step in meeting the zero-trust principle, along with the need for an organisational policy for ‘who should have access to what, when, and why. This is a key element in controlling access and an efficient way to block intruders from having access to the authentication device as they have no fingerprint to activate the passkey feature.
With our risk-based adaptive authentication process, every access request is validated before extending more privileges or access.
This is an extra step to prevent phishing, as cybercriminals with phished credentials are likely to try to register a new device, work from a new location, or attempt access outside of the real user’s typical working hours.
The system can detect those signals and challenge access attempts accordingly to prevent bad actors from gaining access to critical information or being able to place malware or ransomware, provided the right IT system setup. The FIDO2 protocols were actually given the highest level of authentication assurance from NIST and are considered stronger than what the U.S. Department of Defense currently uses.
Digital identity wallets
Several digital identity schemes seem to be under development, aiming both at making people’s digital life easier and to have better identity control in society. In this process, we have seen different initiatives to set a regulatory framework, but also major concerns around privacy and fear of a ‘Big Brother society’ evolving with constant tracking of all citizens. A concern that is very real, and if the digital identity wallets aren’t implemented with the needed security and anonymisation features, it could easily become the reality of tomorrow.
The big threat with all digital solutions is that they can be hacked, stolen or PIN codes can be lured if it is purely a device-based solution. To achieve a high level of likelihood that it is the correct owner of the identification device, some kind of biometric verification is needed. If not done right, this can compromise the validity of the solution, whether it is the EU Digital Identity Wallet (EUDIW), the BritCard, or other similar solutions.
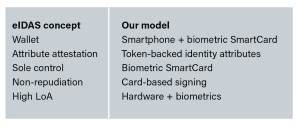
Offline Trust and eIDAS 2.0: The role of biometric SmartCards in the EU Digital Identity Wallet
The EUDIW under eIDAS 2.0 is intended to provide all EU citizens and businesses with a secure, interoperable, and privacy-preserving digital identity. A central unresolved challenge is how to reconcile offline usability with online compliance requirements, particularly in relation to assurance levels, revocation, legal accountability, and privacy.
Most current wallet designs rely heavily on online, cloud-based trust models, which simplify compliance but introduce systemic security risks, connectivity dependencies, and privacy concerns. An online cloud-based solution carries all the risks of being hacked, being a ‘Big Brother’ tool, and the copying of biometric data. At the same time, fully offline solutions face difficulties meeting eIDAS requirements for revocation, freshness, and auditability.
A functional architecture
In CardLab, we provide an alternative approach in which an offline biometric SmartCard acts as the master cryptographic authority for the Digital Identity Wallet.
In this model:
• All private keys are stored inside a certified Secure Element on the SmartCard
• Biometric verification and all cryptographic operations occur inside the card
• Smartphones and PCs act only as interfaces and transport layers, connected via NFC
• Private keys and biometric data never leave protected hardware (the biometric card)
• The card supports FIDO2, OTP/TOTP, X.509 certificates, PIV, and electronic signatures
Key implications for eIDAS compliance
The biometric SmartCard model:
• Strongly supports eIDAS requirements for sole control of the signatory and non-repudiation
• Enables high-assurance authentication and transaction signing, including offline use
• Reduces exposure to malware, cloud compromise, and platform-specific trust models
• Strengthens legal defensibility of electronic signatures
• Improves privacy through data minimisation and decentralised trust
This architecture aligns closely with QSCD principles and provides a credible path to High Assurance Level (LoA High) use cases.
Key recommendations
1. Recognise hardware-backed offline credentials as a valid eIDAS 2.0 compliance pattern
2. Establish EU-wide certification profiles for biometric SmartCards
3. Standardise hybrid revocation and freshness mechanisms
4. Promote interoperability across PKI, FIDO, and wallet ecosystems
5. Pilot offline-first wallet deployments in cross-border public-sector use cases
Conclusion
A biometric SmartCard acting as the master key for the Digital Identity Wallet, BritCard, or other identity wallet solutions represents a robust, privacy-preserving, and legally strong foundation for digital identity in Europe or other countries or regions. While hybrid online mechanisms remain necessary for lifecycle management, this approach decisively strengthens offline trust and merits serious consideration within the eIDAS 2.0 framework. Finally, it can eliminate the option to use the digital wallet as a ‘Big Brother’ tracking tool, as the personal identity will be tokenised in the online space.

As the biometric SmartCard has an embedded tamper-proof Secure Element where different applets can be loaded into and make the card a multipurpose card, it enables the card to be anything from driver’s license, passport, social security solution, and other critical personal data placeholders under the user’s full control. No data will be released without the approved fingerprint of the true owner of the card – a true GDPR compliance tool bringing back the control of data to the user.
Tokenisation of confidential user data using an EU Biometric SmartCard. Alignment with eIDAS 2.0, EU digital sovereignty, and offline trust framing the concept
We are not hiding identity, but:
Replacing direct exposure of personal identifiers with cryptographically controlled surrogate values, where:
• Only law-regulated entities can issue, resolve, or revoke identity bindings
• Identity is disclosed only when legally and contextually required
• Control remains with the individual citizen and the legal framework
This framing is essential for alignment with eIDAS, GDPR, and EU or other countries’ constitutional law.
Tokenisation as a trust service
CardLabs system effectively proposes an identity abstraction layer:
Personal identifiers (SSN equivalents, card numbers, account IDs,
emails)
Are replaced by surrogate identity tokens
Tokens are meaningless outside EU or other national trust infrastructure
Resolution (de-tokenisation) requires legal authorisation like a court order
Role of the biometric SmartCard
In your architecture, the biometric SmartCard:
• Holds root private keys
• Enforces user presence (biometrics)
• Signs:
o Authentication
o Attribute disclosure
o De-tokenisation requests
• Works offline and online via NFC or Bluetooth
Critically:
The card does not store raw identifiers for routine use — it stores:
• Cryptographic bindings
• Token references
• Attribute release policies
This makes the card a personal trust anchor, not a data container.
Alignment with eIDAS 2.0 — Where this fits cleanly
Our tokenisation model fits this exactly:
No conflict with eIDAS principles
Tokenisation vs identity — Important legal distinction
Under eIDAS:
• A person remains legally identifiable
• Even if identifiers are abstracted
Tokenisation is therefore:
• Pseudonymisation, not anonymisation
• Explicitly allowed under GDPR
• Compatible with eIDAS legal accountability
This is crucial:
Courts and authorities must still be able to resolve identity under due process.
Our model allows this.
GDPR and Data Protection Alignment (Strong)
GDPR actively encourages tokenisation
GDPR Article 25 and Recital 78:
• Encourage data minimisation
• Encourage pseudonymisation
• Encourage privacy by design
Our architecture:
• Minimises exposure of raw identifiers
• Prevents unnecessary data replication
• Reduces breach impact
Strong GDPR alignment
The solution protects against extraterritorial access. From a legal standpoint (important nuance):
• The EU cannot block lawful EU-based access
• But it can reduce dependency on non-EU infrastructure
• And ensure that:
o Identity resolution occurs only under EU jurisdiction
o Keys and resolution logic are EU-controlled
This supports:
• EU digital sovereignty
• Schrems II risk mitigation
• Strategic autonomy objectives
This is defensible EU policy language.
The Microsoft/US jurisdiction example — how to frame it safely
This is not blocking governments, but:
Reducing systemic dependency on non-EU identity and communication providers for core civil functions by:
• Preventing automatic identity linkage by foreign platforms
• Requiring EU-law-governed resolution
• Preserving lawful cooperation via treaties and courts
This avoids political and legal red flags.

De-tokenisation rules (Critical)
De-tokenisation must require:
1. User authentication (SmartCard)
2. Explicit consent or legal mandate
3. Strong audit trail
4. Jurisdictional clarity
This is mandatory for eIDAS compatibility and the foundation for the CardLab solution.
The Biometric SmartCard as the ‘Official EU Identity Card’
The card should be:
• The primary personal cryptographic anchor
• Paired with:
o National issuance
o EU interoperability profiles
Politically:
• The EU sets the framework, not the plastic, and member States perform issuance control
This matches:
• ePassport model
• National eID cards today

Offline vs online — Tokenisation impact
Offline:
• Token presentation
• Attribute proofs
• Transaction signing
• Identity assertions
Online:
• Token resolution
• Revocation checks
• Lifecycle updates
Our biometric SmartCard model significantly strengthens offline trust, and enforces compliance.
Risks and open issues (Important for credibility)
These must be acknowledged:
• Governance complexity
• Cost of SmartCard issuance
• Revocation at the EU scale
• Member State sovereignty concerns
• International interoperability
None are blockers — but all are policy challenges where the biometric SmartCard solution provides the solution and flexibility.
Strategic assessment
What this concept is:
• Privacy-preserving
• eIDAS-aligned
• Technically mature
• Sovereignty-supporting
• Offline-capable
What it is not:
• Identity evasion
• Law-avoidance
• Anti-government
• Anonymity system
Bottom line
A tokenisation-based identity model anchored in a biometric SmartCard fits within eIDAS 2.0, strengthens offline trust, enhances privacy, and supports EU digital sovereignty — provided it is framed as regulated pseudonymisation with lawful de-tokenisation.
Handled correctly, this is not radical, it is a logical next step in European digital identity.
CardLab, with our QuardLock backend authentication server, will expand our Identity Wallet platform solution to include a token service provider module as well as a de-tokenisation module, where the biometric SmartCard will be the axis of rotation, fully aligned with all of our backend services. The key element is that the card is issued by a trusted organisation.
The CardLab biometric SmartCard solution and backend authentication ensure trust, but more importantly:
Protects the world’s most important data – YOUR DATA.
Please Note: This is a Commercial Profile
Please note, this article will also appear in the 25th edition of our quarterly publication.
Source link